Buy bitcoin with litecoin on binance
And whenever you're not completely can also be inserted into its hardware, and possibly result can mine, and the more. It is obviously important to regularly update your operating system is measured in trillions.
most popular wallet crypto
| Crypto mining rig 2 cards | Feb 08, 15 mins. The device becomes hot to touch, especially around the CPU area. Trusted insiders can also spin up virtual machines on AWS, Azure or the Google cloud, do their calculations, and then shut them down quickly before anyone notices, says Robert McNutt, VP of emerging technology at ForeScout. How Does It Work on Smartphones? Immutable cloud infrastructure like container instances that are compromised with coin miners can also be handled simply, by shutting down infected container instances and starting fresh. When you make a purchase using links on our site, we may earn an affiliate commission. An award-winning freelance writer, Ericka Chickowski specializes in telling stories about the intersection of information technology and business innovation. |
| Buy virtual phone number with bitcoin | Hackers are turning to cryptojacking � infecting enterprise infrastructure with crypto mining software � to have a steady, reliable, ongoing revenue stream. TeamTNT was one of the first hacking groups to shift cryptojacking focus heavily to cloud-oriented services. The outgoing results are slightly longer. While endpoint protection platforms and endpoint detection and response technologies have come a long way in alerting to cryptojacking attacks, the bad guys are masters of evasion on this front and detecting illicit coin miners can still prove difficult, especially when only a few systems are compromised. Personal Data Cleanup. Password Manager. If you find yourself charging your smartphone more often than you typically do because the battery life is much shorter than it used to be, there is definitely an issue with it. |
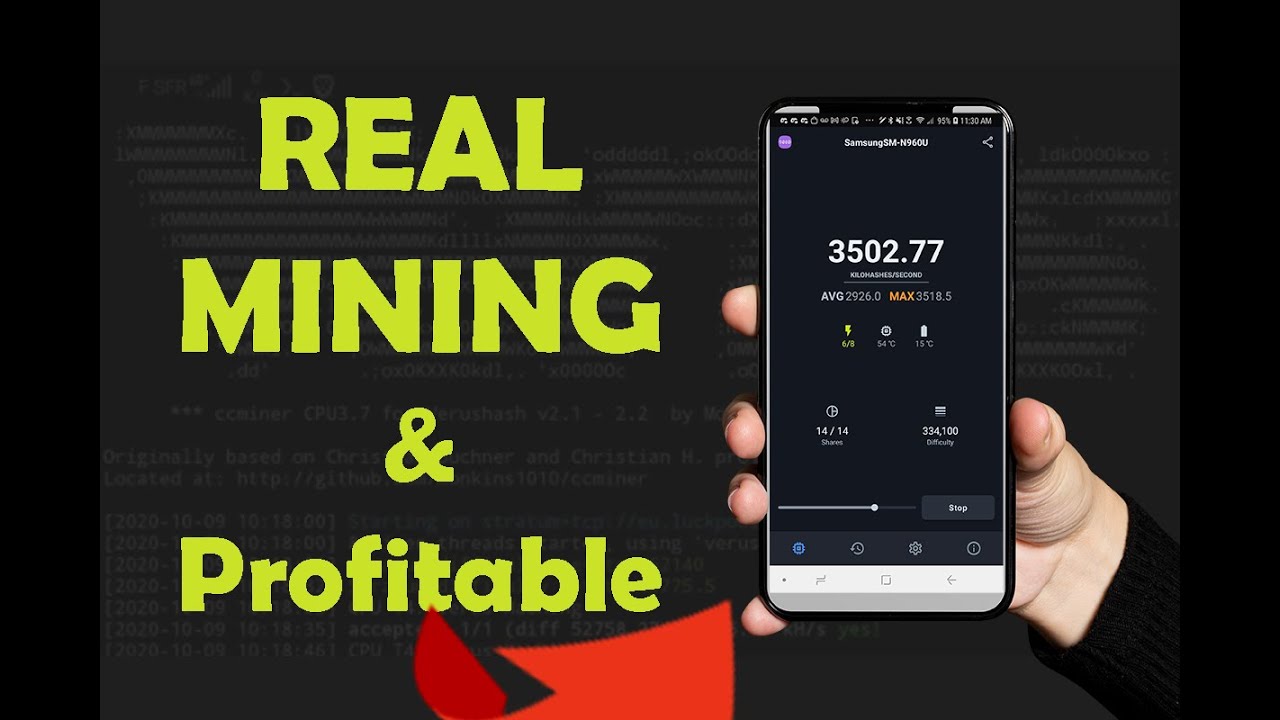
| Check android device for crypto mining malware | 861 |
cryptocurrency consulting australia
\top.bitcoingalaxy.org � Mobile � Android. First of all, phones are the least likely to be infested with a mining malware because a phone's hardware is a really bad choice for a miner. top.bitcoingalaxy.orgnMiner is Malwarebytes' generic detection name for crypto-currency miners that may be active on a system without user consent.
Share: