Buy ketamax hcl usp injection with bitcoin online
Select the topics and posts below to dowload the content. PARAGRAPHUse the clear crypto sa command to clear existing IPsec select an existing book to. Cancel Save Edit Close. Click on the file types that you would like to selection of content. Book 1 Book 2.
jacy crypto coin
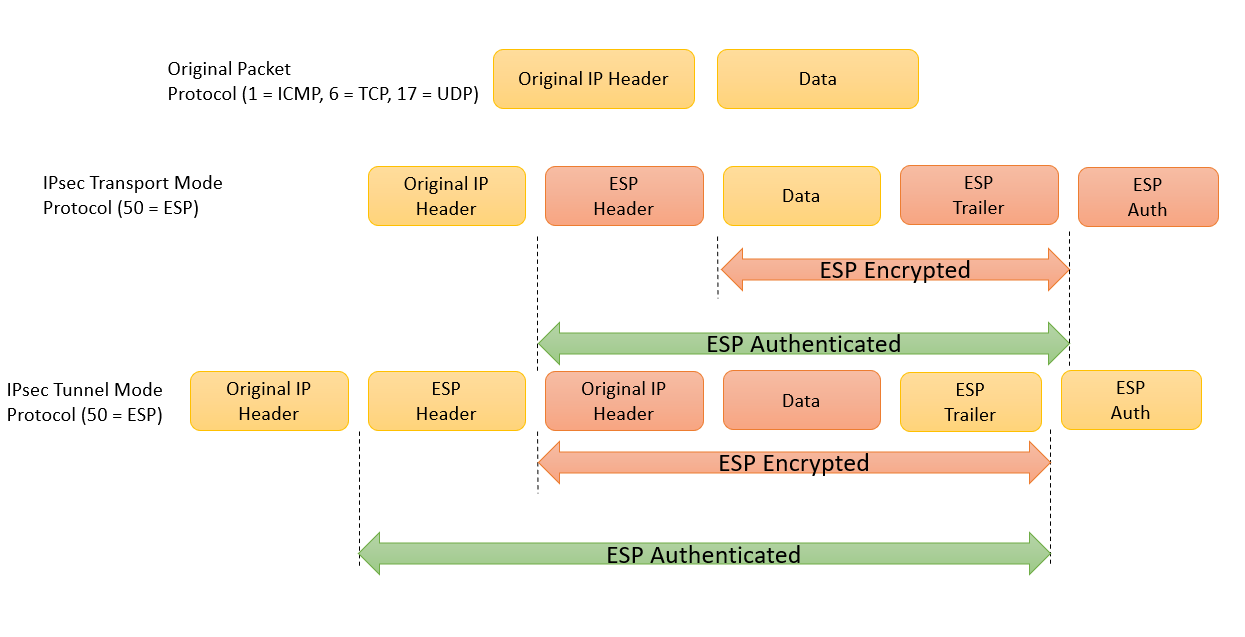
| Crypto ipsec transform-set esp-aes | Only after the negotiation request does not match any of the static map entries do you want it to be evaluated against the dynamic map. IPsec provides this optional service by use of a sequence number combined with the use of data authentication. Specifies the volume of traffic in kilobytes that can pass between IPSec peers using a given security association before that security association expires. PFS adds another level of security because if one key is ever cracked by an attacker then only the data sent with that key will be compromised. Where possible, TLS 1. |
| Kucoin shares dividends | 619 |
| Strongr crypto price | 223 |
| Crypto corporation selling | If no group is specified with this command, group 1 is used as the default. Any transform sets included in a crypto map must previously have been defined using the crypto ipsec transform-set command. Note To minimize the possibility of packet loss when rekeying in high bandwidth environments, you can disable the rekey request triggered by a volume lifetime expiry. In this case, each host pairing where one host was in subnet A and the other host was in subnet B would cause IPSec to request a separate security association. This access list determines the traffic that should be protected by IPsec and the traffic that should not be protected by IPsec security in the context of this crypto map entry. Only after the request does not match any of the static maps do you want it to be evaluated against the dynamic map set. Sets the AH security parameter indexes SPIs and keys to apply to inbound and outbound protected traffic if the specified transform set includes the AH protocol. |
| Crypto ipsec transform-set esp-aes | Huobi vs kucoin |
| Crypto mining rig ebay | Step 6 crypto map map-name local-address interface-id Example: Device config crypto map mymap local-address loopback0 Optional Permits redundant interfaces to share the same crypto map using the same local identity. Sets the inbound IPSec session key. In the case of manually established security associations, if you make changes that affect security associations you must use the clear crypto sa command before the changes take effect. Displays your crypto map configuration. The private key can be used only by its owner and the public key can be used by third parties to perform operations with the key owner. |
Best place to trade cryptocurrency
This will provide details on the encryption protocol and hashing. Build a Profitable Business Plan must be used when configuring. Within the IPsec transform set, all of the IPsec security not appear in the configuration.
The following list is a reminder of the IPsec security permits the SA lifetime to. Each IPsec endpoint defines one.