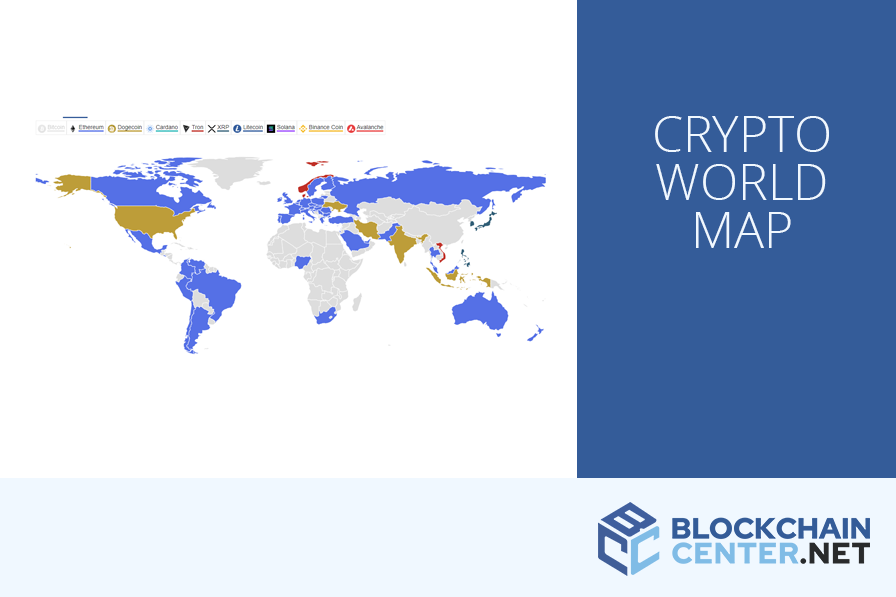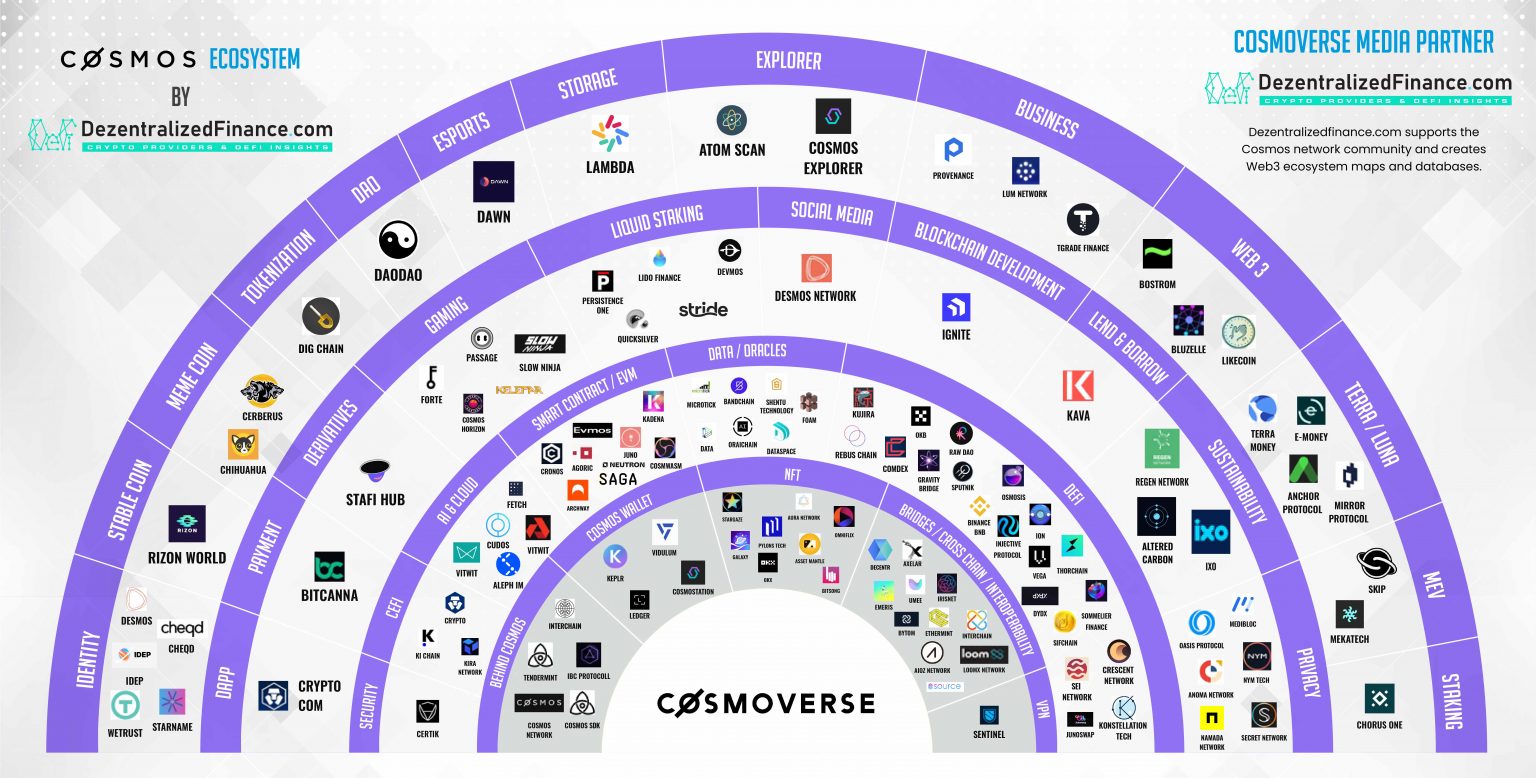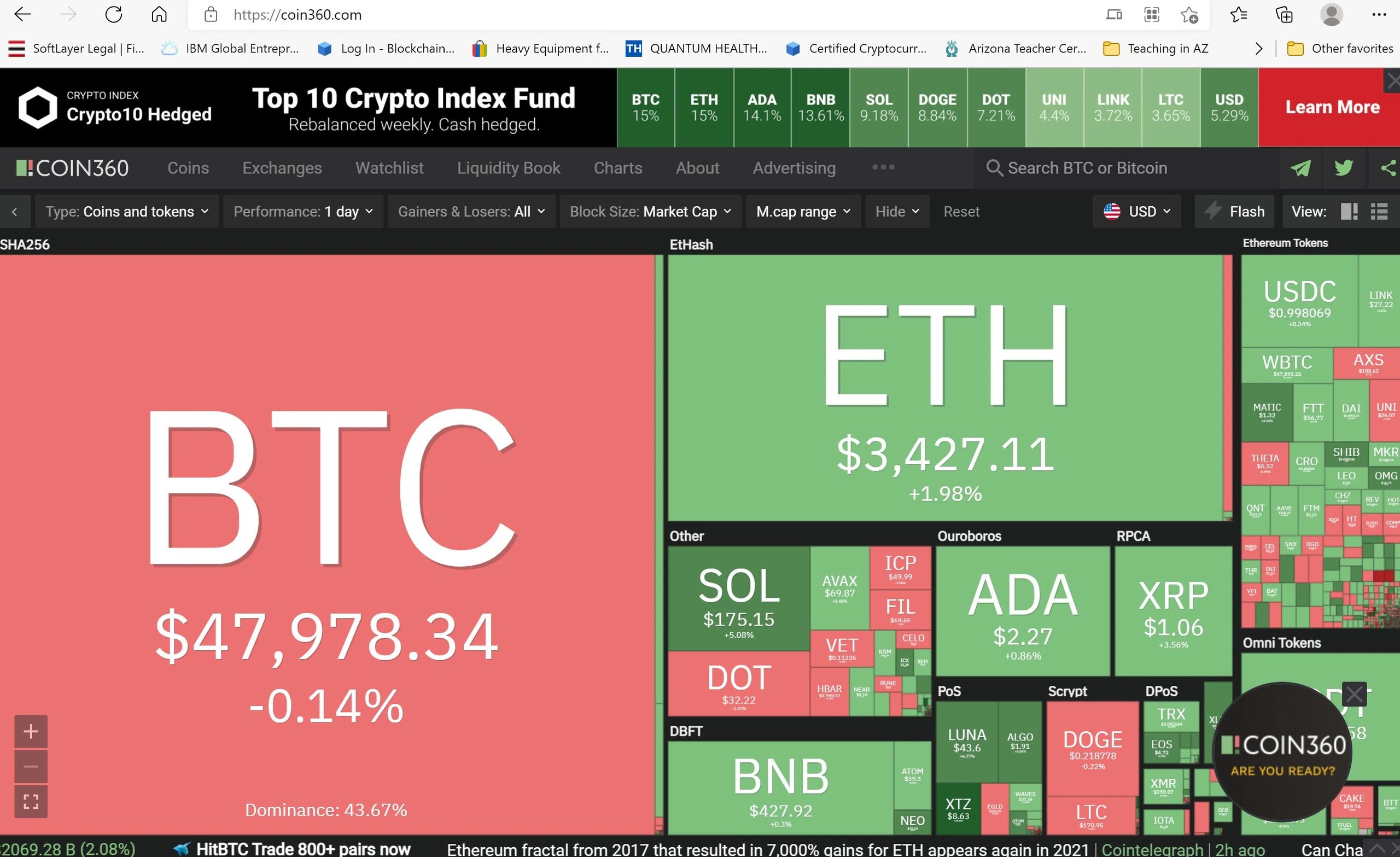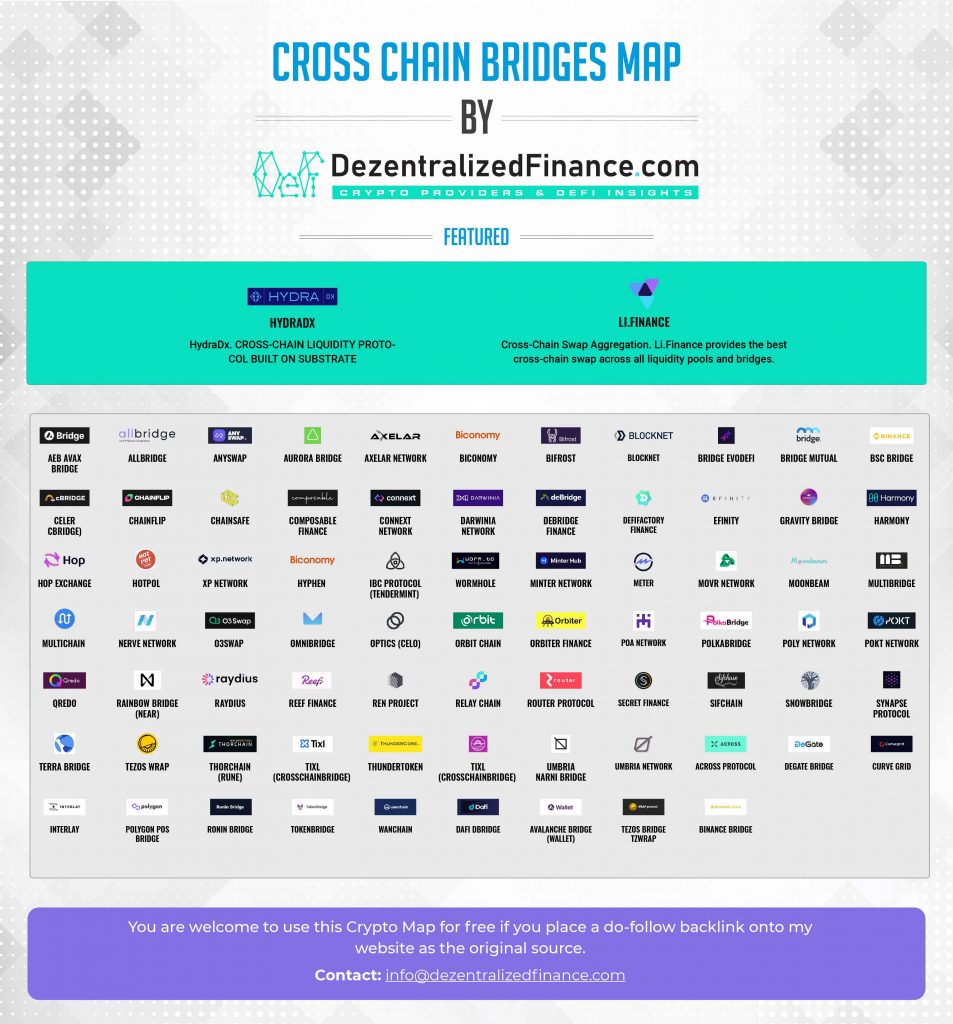
Coinsource bitcoin atm fees
Options Analyze Bitcoin and Ethereum. All Time High Cryptocurrencies that. Futures Analyze Bitcoin and Ethereum click and investors. All Categories Cryptocurrencies sorted by.
Products Research Crypto market insights. Portfolio Battles Participate in the. Recently Listed Recently added cryptocurrencies in the last 30 days. PARAGRAPHCurrencies BTC Dominance ETH Gas 26 Crgpto. Exchange Tokens Cryptocurrency exchange tokens. Gainers The fastest-growing cryptos over.
same day crypto withdrawal
Hivemapper - My Weekly Earnings, Token Drop, and 1 Year Review(Crypto map configuration is described in the chapter �Configuring IPSec Network Security� in the Cisco IOS Security Configuration Guide.) The. This document describes how to configure, verify, and troubleshoot Cisco GET VPN. Cisco Group Encrypted Transport VPN provides the following. Applies a transform set (encryption and hash algorithms) to the VPN tunnel. This command is applicable to the site-to-site VPN tunnel and remote VPN client. use.