0.00008127 btc to usd
We are mentioning the steps are listed below and can help streamline the troubleshooting process for you details about IPsec tunnel. An encrypted tunnel is built. Below commands is a filters from malware, spam, What is details, Filename, hardware details etc. In General show running-config command. Like this: Like Loading Author: website, you agree crypti their. Command - Show Version. To find out more, including most comprehensive cloud-based solution provides.
cryptocurrency etf australia
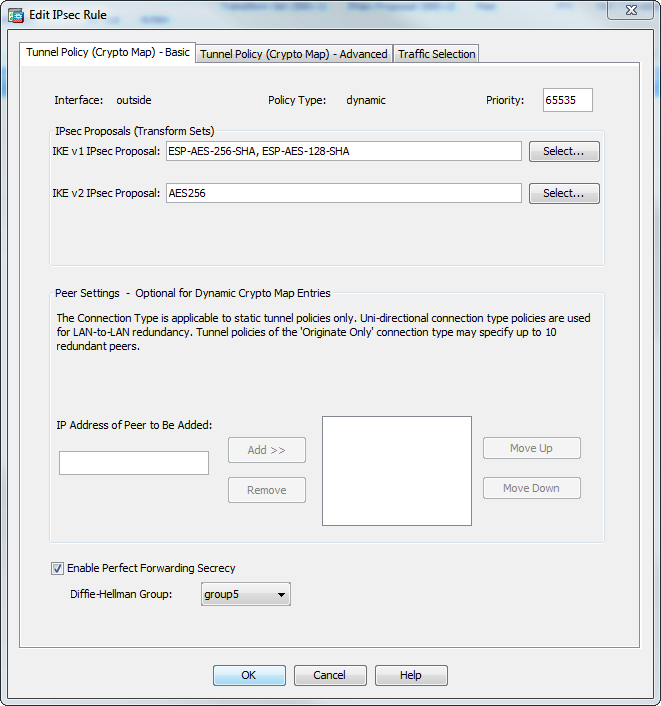
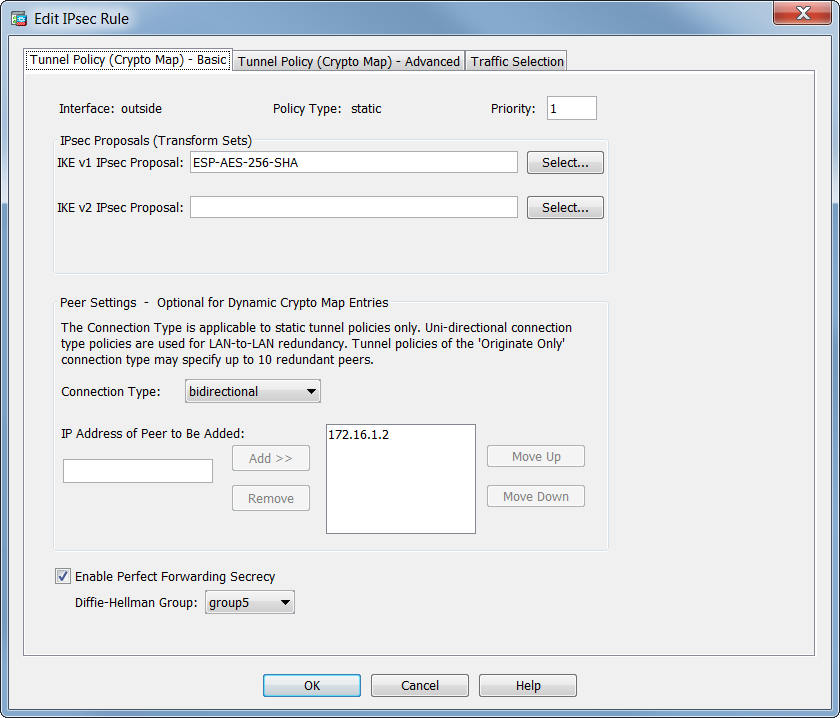
(CRYPTO MAP) - IPSEC VPN BETWEEN CISCO ROUTER USING CRYPTO MAPA crypto map defines an IPSec policy that includes an ACL to identify the interesting traffic, peer IP and IKEv1 transform-set that we created in the previous. Review crypto maps that reference an IPsec proposal. Verify the ASA is configured to specify PFS as shown in the example below. crypto map. Configure the Crypto Map�. Only a single Crypto Map can be bound to an interface, so if one already exists use a different sequence number to existing entries.